DDoS attacks are on the rise, steadily increasing annually. Email bombs, which are categorized as denial-of-service or DoS attacks, are one such example.
This dangerous practice sends emails in large quantities and is usually done to focus attention away from ongoing security breaches.
Businesses, especially startups and small companies, must be warier than ever in today’s digital environment.
Being on the receiving end of an email bomb means losing subscribers, as your customers should unsubscribe from your email list to avoid potentially being exposed to more trouble. Your email deliverability can also take a nosedive, affecting your sender’s reputation.
As you can see, becoming cognizant of email bombs, including knowing how to recognize them and when you could be at risk, is a major component of safely running a small business.
In this blog post, we’ll learn what an email bomb is, the types, the dangers, steps to identify, and preventative measures.
Table of Contents
Key Takeaways
- Email bombs can happen to any small business owner, wreaking havoc on your reputation and email deliverability rates.
- The top preventative measures every small business should implement are using CAPTCHAs, monitoring for abnormal activity, patching your email systems as required, and improving your email filters.
What Is an Email Bomb?
Email bombs are DoS attacks, meaning a cyber threat prevents the victim from using network resources, devices, or systems. In this case, it’s an email system. A bot will send so many emails to one address that the victim can’t do much of anything.
If they receive security breach notifications, they’ll get buried in the deluge of emails, leaving them unable to check the notifications, let alone act. Sometimes, the barrage is so much that the victim can’t use their email.
Email bombs can even render the server unusable if the email quantity is large and rapid enough.
The reason bots are deployed for email bombing is that they can send emails at a fast enough rate to pull off the attack successfully. The number of emails sent can be hundreds to thousands and in only a minute or several.
The types of emails vary but often include subscription confirmations. Most of the time, an email bomb recipient is not chosen at random, but is a targeted individual. However, in other cases, someone can be targeted if attacking them can overload the email server, so it seems more random.
Being bombarded with massive numbers of emails is rarely the only problem that occurs during an email bombing. For example, a security breach can occur right under your nose because you’re too worried about being flooded with emails. Fraud is another risk.
In that regard, the email bomb is more like a smokescreen that deters your attention from the real threat.
Why do email bombings occur?
The primary motivator for email bombings is to harm an individual online, or at least damage their reputation. Rarely are companies targeted, but rather specific persons.
Email bombings can occur to gain access to sensitive or proprietary information or to expose the victim to malware and phishing schemes.
Read more: The Impact of Spam Complaint Rates on Email Deliverability (And How to Fix It)
The Types of Email Bombs
Most email bombs are malicious, but they’re not all created equally. Here are the various types of mass email spam you could receive.
Zip bombing
When you’re zip-bombed, you’ll receive a file that is overly large but compressed using tools like 7-Zip or WinZip. The text file may only consist of a single letter or large portions of font, but it’s a bloated file with millions of characters.
Zipping tools can compress the file to a size small enough to send via email. Once you receive and access the file, unpacking it launches the DoS attack. Early email servers were especially susceptible to zip bombing.
Here’s another interesting fact. Sending tar.gz files or ZIPs can make a copy of the file, meaning that if the email server looked for nested archive files, infinite incursion could occur, starting an endless loop.
List linking
The next type of email bombing to be wary of is list linking, sometimes called email cluster bombing. The victim will have their email address submitted to various subscription services.
Identifying the attacker can be very difficult, especially since the scripts to execute a list-linking attack are simple to set up. To free yourself from the emails you don’t want to receive from the subscription services you didn’t sign up for, you can either abandon the email address or manually unsubscribe from each.
Although many businesses now require subscribers to confirm that they want to join the list to ward off list linking, a high rate of confirmation emails following a message announcing a subscription to the service only further buries the victim in emails.
Mass mailing
The last type of email bombing is mass mailing. One email address will receive a multitude of emails simultaneously as part of a DoS or DDoS attack. Zombie botnets led by a perpetrator can be commanded to send millions of messages to various email addresses, typically business email accounts and website host accounts.
Using zombie botnets makes mass mailing harder to defend against, but simpler mass-mailing scripts can be stopped by spam filters.
Read also: Avoiding the Spam Folder — An Intro to Email Deliverability
The Impact of Email Bombing on Small Businesses
As I alluded to in the intro, becoming the victim of an email bombing can have major negative ramifications for small businesses and startups. Let’s take a look.
Loss of subscribers
If your customers are targeted rather than your business, any IT person worth their salt will tell them to unsubscribe from your email list after being bombed. Once that happens, the customer is unlikely to resubscribe, considering the severity of the incident.
More spam complaints
What’s worse is that many recommendations for handling spam traps also advise reporting the email address for spam.
Your business email could begin generating many spam complaints, even if you didn’t do the email bombing, because of your association with what happened.
Eroded audience trust
Email bombing is a serious cyber offense.
Even if you didn’t do anything to warrant the attack, it still happened to you, which is scary for your audience. They may worry that their data could be leaked or the attacker could come for them next time.
As a result, you might lose subscribers beyond those involved in the attack. You may also notice a decrease in leads immediately following the attack.
Potential data breach
Since email bombs are used to distract from the crimes a cybercriminal is truly committing, a data breach could follow soon after. If so, the breach can lead to a possible loss of proprietary data and personal customer information.
While breaches happen constantly, with 353 million individuals affected in 2023, that doesn’t make them a less bitter pill to swallow. Your audience will lose their faith in you, at least temporarily, and you could also deal with…
Brand reputation damage
Breaches are big business, so when they happen, they tend to get reported on in print and visual media, such as television news. Your brand will be all over the place for the next few weeks, but not in a good way.
Fortunately, you can repair your brand again after a data breach from an email bombing, but it will take time and patience above all else.
Read also: What Is Domain Reputation and How Can You Improve It?
Diminished sender reputation
Besides your brand reputation, your sender reputation will also take a hard hit.
Your sender reputation is determined by internet service providers or ISPs. It’s based on factors like whether you stay off spam traps, how receptive your audience is to the messages you send, how many emails you send daily, whether you buy or obtain your lists organically, and similar factors.
Prioritizing email hygiene is usually enough to maintain your sender reputation, but becoming the victim of an email bomb attack can throw it out of whack. While you practice good email habits and wait for your reputation to renew, you will likely experience email deliverability issues.
Loss of time
Email bombing is scary, and it’s also a time-suck, especially in the aftermath. First, you have to survey the damage. You also have to manually unsubscribe from however many services your email address ended up associated with.
You might need computer repairs for malware and viruses, and if you have to seek legal counsel, that’s yet more time you lose.
Reduced productivity
It’s no surprise that when an email bombing occurs, and usually in the direct aftermath, you can’t get a thing done. You won’t be able to make heads or tails of your inbox until the bombing stops.
When it finishes, you still must manually go through all those emails you received, hampering productivity for longer.
Potential legal costs
If you can track down who instigated the email bombing, you might decide to defend your rights legally. If so, the legal costs can rack up between thousands to tens of thousands, depending on the scope of the case.
Read more: Email Deliverability — 7 Tips to Get More Clicks, Sells & Signups
How to Identify an Email Bomb
Recognizing potential email bombs can be difficult, but the following tips can make you savvier.
Monitor your email traffic for anomalies
Getting to the source of an email bomb starts with historical data.
Did you have any email irregularities in the days leading up to the attack? This could be related and help you precipitate and prepare for a future attack.
Get good at sniffing out suspicious emails
Going with your gut can save you a lot of stress and headaches.
If an email gives you a bad feeling, there’s nothing wrong with sending it to the trash without opening or reading it. If you know the sender, ask them (via phone or another communication channel) to send you another email.
Use tools to detect unusual email activities
With so many tools on the market that notify you of potentially suspicious email activity, you shouldn’t have to be caught off-guard by an email bomb.
Here’s a rundown of solutions to explore:
- Discoverly
- MailerSend
- Checker Plus
- LinkedIn Sales Navigator
- Mailtrack
- Mailshake
- MailTracker by Hunter
- HubSpot Sales
- Veriato
- Batch Reply
- Proofpoint
- Streak
- Yesware
- Gmelius
- Just Not Sorry
- Cirrus Insight
- Dittach
- ActiveInbox
- InterGuard
- Find Big Mail
- Saleshandy
- Sortd
- Teramind
- me
- Mailstrom
- Boomerang
Read more: Top Tools & Strategies to Improve Email Delivery Rates
Preventative Measures and Best Practices to Keep Email Bombs at Bay
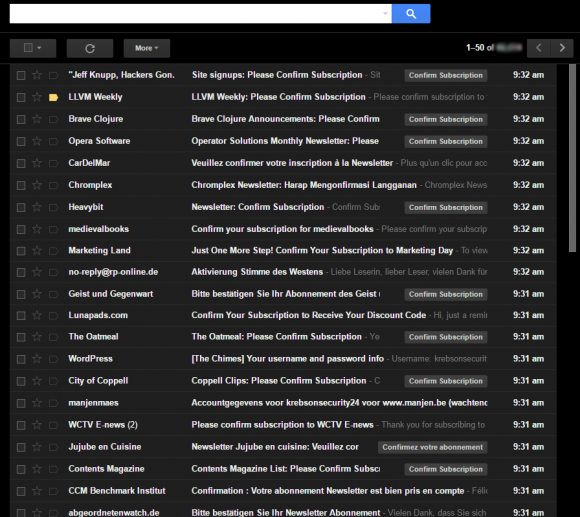
Besides the above, these comprehensive strategies will protect your small business from email bombs.
Implement strong email filters
Email filtering is a reliable tactic for combatting spam, and more so, it can stop malware and viruses dead in their tracks.
How does it work?
You’d invest in an email filtering service to get your outgoing emails before they reach their intended recipients. Likewise, when someone emails you, it first goes through the email filter.
If all is good, the filter allows the email to your inbox or someone else’s. However, if the email is malware or a spam risk, the filter will catch it.
And how does an email filter determine which emails are risky versus which are okay? It will check for criteria like:
- Redirected and/or shortened links in the email, which may be signs of spam or a possible email bomb.
- The instance of spam terms, especially in the subject line or when used frequently.
- The rate of emails being sent from a recipient may indicate spam and/or an email bomb.
- The domain reputation of the email address sending the message; if it’s low, an email filter might not let a message go through.
- The IP address of the email can be marked as spam if it has a poor reputation.
Use CAPTCHA on subscription forms
I mentioned earlier how email services have begun implementing confirmations to ensure that people only sign up for the email lists of their own volition and aren’t being unwittingly subscribed as part of an email bomb.
While well-intentioned, you’ll also recall that these confirmation emails end up causing more harm than anything else. They are just further email spam a victim must deal with after an email bombing.
CAPTCHA is a more reliable way to ensure your email list is filled only with willing participants. I’m sure you’ve seen and partook in these before, but CAPTCHAs are quick Turing tests that require you to rotate images to match the one in the example or select only images with cars or another subject.
reCAPTCHA is Google’s free CAPTCHA service you can implement when allowing people to subscribe to your emails. It’s too much trouble for nefarious characters to pass the CAPTCHA when trying to email bomb someone else.
Regularly update and patch your email systems
While you’re on the right track in resisting email bombs, you can’t rest on your laurels. You must continuously monitor and update your email systems, patching as required.
Bad cyber actors need only one chink in your armor to penetrate it and take over, potentially leaking customer or proprietary data. Don’t even give them the opportunity.
Provide employee training on cybersecurity practices
You should also sit your team down to a seminar or instructional video explaining cybersecurity, what kinds of cyber threats are out there, and how to identify them. If you’ve experienced an email bombing, explain what happened in full so your team understands the severity.
Additionally, emphasize the importance of using a VPN to protect sensitive data when accessing the internet, especially on public networks.
Next, discuss which preventative strategies your small business will take to safeguard you from email bombs and other cyber threats. If required, provide training on the new tactics and monitor your team to see if they need assistance acclimating.
Read more: Prioritizing Email List Quality — The Road to Higher Open Rates
Steps to Take If You’re a Victim of an Email Bomb
What protocol should you follow if you’ve been email bombed? Let’s review.
Review the extent of the damage
You just got rocked. There were so many emails, one after another, that you thought the onslaught would never stop. Now that it has, you’re unsure how to go through the flurry of emails.
You don’t have to, at least not right this moment. For now, determine what transpired and how severe it is. Remember that the incident’s true severity might not reveal itself for days, weeks, or months if your data was breached and sensitive information stolen.
Reach out to your email provider
The next order to do business is to contact your email provider and/or system administrator to inform them of what happened. They should be aware, as they can recommend and implement immediate safeguards. They can also help you remove all the junk emails, saving you time.
Change your passwords
You don’t know if the cybercriminal obtained your business passwords, but just in case, it doesn’t hurt to change them. While I hope your email passwords are unique to the other passwords your small business uses, if they aren’t, you need to change those passwords, too.
This time, set a more secure password using random numbers, characters, and letters. Try a free random password generator if you’re struggling to think of something.
Inform your audience
This is arguably the hardest part. There is no way to admit what happened without looking bad, but that doesn’t mean hiding the truth from your customers is a good idea, either. Even if they weren’t directly affected, you should still inform them about the email bombing, as their information could be part of a breach.
And was your audience directly email-bombed? Send them instructions on what to do, and be aware that you’ll likely lose them as email subscribers for good (and thus likely customers).
Contact your vendors and partners
It also doesn’t hurt to drop a line to any partners and vendors you work directly with, especially if you worry that their information could be leaked, or you could be patching up reputational damage in the coming months.
Keeping your partners abreast of what may be going on is a common courtesy. Even if nothing further transpires beyond the email bombing, they’ll appreciate that you kept them in the loop.
Continue monitoring
Use email monitoring, credit monitoring, and financial tools in the months ahead to ensure everything remains stable.
Read also: How to Prevent Getting Caught in Google Spam Filters
Conclusion
Email bombs are scary phenomena, and they’re more frequent than you might think.
Your small business must be prepared for the potential of being bombed. Even if it never happens, considering the severe consequences, you’ll be glad you prioritized hypervigilance and proactivity in your cybersecurity efforts.
EngageBay is an all-in-one marketing, sales, and customer support software for small businesses, startups, and solopreneurs. You get email marketing, marketing automation, landing page and email templates, segmentation and personalization, sales pipelines, live chat, and more.
Sign up for free with EngageBay or book a demo with our experts.
Frequently Asked Questions (FAQ)
1. What is the difference between an email bomb and a spam email?
One of the primary differences has to do with frequency. A spam email is one message sent occasionally, whereas an email bomb is hundreds to thousands of emails dropped simultaneously.
The targets are also different. Spam emails are sent to people rather undiscerningly, whereas email bombing has a target victim in mind.
2. How can I legally protect my business from the effects of an email bomb?
It helps if you have a business lawyer specializing in cybersecurity who can advise you on the best legal course of action in case of an email bomb.
3. What are the common signs of an email bomb?
The biggest and most substantive sign of being email bombed is receiving hundreds or thousands of email messages for services you didn’t subscribe to.
The emails will come in fast and furious, barely allowing you to catch up. You may also receive confirmation requests for each service you subscribe to.
4. Are there any specific industries more at risk of receiving an email bomb?
Not particularly, but the government has been a main target for email bombing in the past, so public-facing industries like that should especially have their security raised.
5. How frequently should I update my email security practices?
A good timeframe for updating your passwords and other email security practices is once every three months.
6. What should I do if my email system has been compromised by an email bomb?
Contact your email system service provider and follow their instructions. They will most likely advise you to change your password.
